Azure RBAC: role assignments and ARM templates

This post is about Azure's role assignments and ARM templates. Role assignments can be thought of as "permissions for Azure".
If you're deploying to Azure, there's a good chance you're using ARM templates to do so. Once you've got past "Hello World", you'll probably find yourself in a situation when you're deploying multiple types of resource to make your solution. For instance, you may be deploying an App Service alongside Key Vault and Storage .
One of the hardest things when it comes to deploying software and having it work, is permissions. Without adequate permissions configured, the most beautiful code can do nothing . Incidentally, this is a good thing. We're deploying to the web; many people are there, not all good. As a different kind of web-head once said:

Azure has great power and suggests you use it wisely .
Access management for cloud resources is critical for any organization that uses the cloud. Azure role-based access control (Azure RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in Azure helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access.
This is good advice. With that in mind, how can we ensure that the different resources we're deploying to Azure can talk to one another?

Role (up for your) assignments
The answer is roles. There's a number of roles that exist in Azure that can be assigned to users, groups, service principals and managed identities. In our own case we're using managed identity for our resources. What we can do is use "role assignments" to give our managed identity access to given resources. Arturo Lucatero gives a great short explanation of this:
Whilst this explanation is delightfully simple, the actual implementation when it comes to ARM templates is a little more involved. Because now it's time to talk "magic" GUIDs. Consider the following truncated ARM template, which gives our managed identity (and hence our App Service which uses this identity) access to Key Vault and Storage:
Let's take a look at these three variables:
The three variables above contain the subscription resource ids for the roles Storage Blob Data Contributor , Key Vault Secrets Officer and Key Vault Crypto Officer . The first question on your mind is likely: "what is ba92f5b4-2d11-453d-a403-e96b0029c9fe and where does it come from?" Great question! Well, each of these GUIDs represents a built-in role in Azure RBAC. The ba92f5b4-2d11-453d-a403-e96b0029c9fe represents the Storage Blob Data Contributor role.
How can I look these up? Well, there's two ways; there's an article which documents them here or you could crack open the Cloud Shell and look up a role by GUID like so:
Or by name like so:
As you can see, the Actions section of the output above (and in even more detail on the linked article ) provides information about what the different roles can do. So if you're looking to enable one Azure resource to talk to another, you should be able to refer to these to identify a role that you might want to use.
Creating a role assignment
So now we understand how you identify the roles in question, let's take the final leap and look at assigning those roles to our managed identity. For each role assignment, you'll need a roleAssignments resource defined that looks like this:
Let's go through the above, significant property by significant property (it's also worth checking the official reference here ):
- type - the type of role assignment we want to create, for a key vault it's "Microsoft.KeyVault/vaults/providers/roleAssignments" , for storage it's "Microsoft.Storage/storageAccounts/providers/roleAssignments" . The pattern is that it's the resource type, followed by "/providers/roleAssignments" .
- dependsOn - before we can create a role assignment, we need the service principal we desire to permission (in our case a managed identity) to exist
- properties.roleDefinitionId - the role that we're assigning, provided as an id. So for this example it's the keyVaultCryptoOfficer variable, which was earlier defined as [subscriptionResourceId('Microsoft.Authorization/roleDefinitions', 'ba92f5b4-2d11-453d-a403-e96b0029c9fe')] . (Note the use of the GUID)
- properties.principalId - the id of the principal we're adding permissions for. In our case this is a managed identity (a type of service principal).
- properties.scope - we're modifying another resource; our key vault isn't defined in this ARM template and we want to specify the resource we're granting permissions to.
- properties.principalType - the type of principal that we're creating an assignment for; in our this is "ServicePrincipal" - our managed identity.
There is an alternate approach that you can use where the type is "Microsoft.Authorization/roleAssignments" . Whilst this also works, it displayed errors in the Azure tooling for VS Code . As such, we've opted not to use that approach in our ARM templates.
Many thanks to the awesome John McCormick who wrangled permissions with me until we bent Azure RBAC to our will.
- Role (up for your) assignments
- Creating a role assignment

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...

- Adding or removing role assignments using Azure Portal
Go back to AZ-304 Tutorials
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
However, Azure’s role-based access control (RBAC) refers to the authorization system for managing access to Azure resources. And, to grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.
Prerequisites
For adding or removing role assignments, you must have:
- Firstly, Microsoft.Authorization/roleAssignments/write
- Secondly, Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
Access control (IAM)
Access control (IAM) is the page that is for assigning roles to grant access to Azure resources. It’s also known as identity and access management and appears in several locations in the Azure portal. There are questions for assigning roles to help in understanding about the Access control (IAM) page.
- Who needs access? This refers to a user, group, service principal, or managed identity.
- What role do they need? Permissions are grouped together into roles, so you can select from a list of several built-in roles orcan use custom roles.
- Where do they need access? This refers to the set of resources that the access applies to. However, “where” can be a management group, subscription, resource group, or a single resource such as a storage account.
Adding a role assignment
- Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to.
- Secondly, click the specific resource for that scope.
- Then, Click Access control (IAM).
- Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
- After that, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
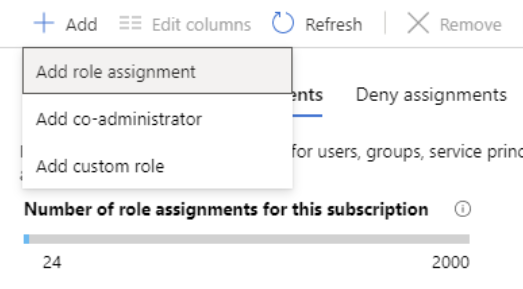
- Then, in the Role drop-down list, select a role such as Virtual Machine Contributor.
- There in the Select list, select a user, group, service principal, or managed identity. And, if you don’t see the security principal in the list, you can type in the Select box to search the directory for display names, email addresses, and object identifiers.
- Lastly, click Save to assign the role.
Assigning a user as an administrator of a subscription
For giving users the role of an administrator of an Azure subscription, first assign them the Owner role at the subscription scope. As the Owner role gives the user full access to all resources in the subscription, including the permission to grant access to others. However, these steps are the same as any other role assignment.
- Firstly, in the Azure portal, click All services and then Subscriptions.
- Then, click the subscription where you want to grant access.
- Thirdly, click Access control (IAM).
- After that, click the Role assignments tab to view the role assignments for this subscription.
- Then, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- And, in the Role drop-down list, select the Owner role.
- Then, in the Select list, select a user.

Adding a role assignment for a managed identity
For adding role assignments for a managed identity use the Access control (IAM) page. However, when you use the Access control (IAM) page, you start with the scope and then select the managed identity and role. In this section, you will learn about an alternate way to add role assignments for a managed identity. Using these steps, you start with the managed identity and then select the scope and role.
System-assigned managed identity
- Use these steps for assigning a role to a system-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a system-assigned managed identity. Then, in the left menu, click Identity.
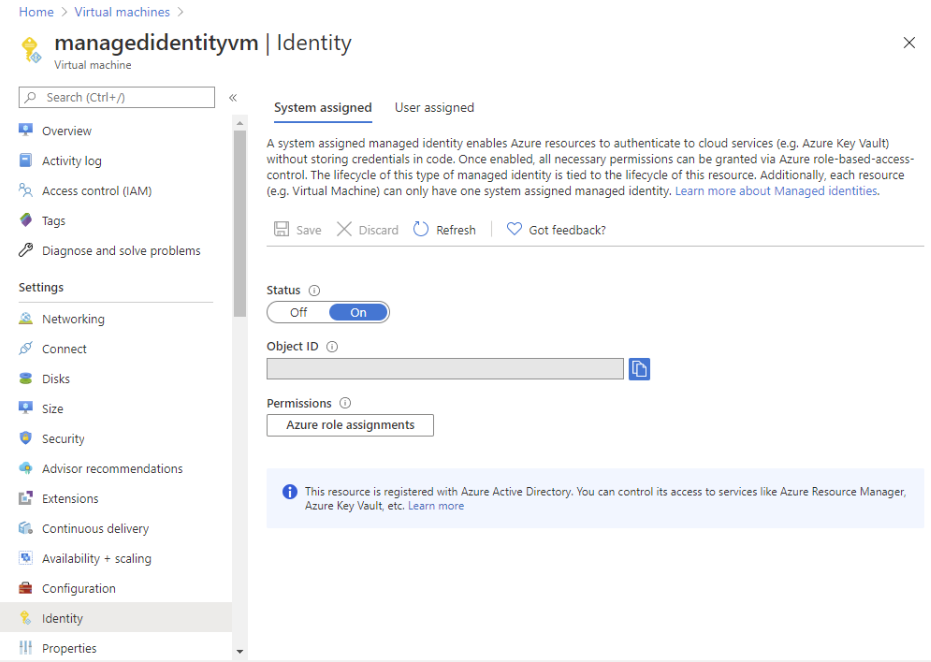
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected system-assigned managed identity then you will see the list of role assignments.
- For changing the subscription, click the Subscription list. Then, click Add role assignment.
- Then, use the drop-down lists to select the set of resources that the role assignment applies to such as Subscription, Resource group, or resource. And, if you don’t have role assignment write permissions for the selected scope, an inline message will be displayed.
- After that, in the Role drop-down list, select a role such as Virtual Machine Contributor.
User-assigned managed identity
- Use these steps for assigning a role to a user-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a user-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected user-assigned managed identity then you will see the list of role assignments.
Removing a role assignment
In Azure RBAC, for removing access from an Azure resource, you first remove a role assignment. Use these steps to remove a role assignment.
- Firstly, Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
- Then, click the Role assignments tab to view all the role assignments for this subscription.
- After that, in the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
- Then, Click Remove.
- Lastly, in the remove role assignment message that appears, click Yes.
However, if you see a message that inherited role assignments cannot be removed, then you are trying to remove a role assignment at a child scope. So, you should open Access control (IAM) at the scope where the role was assigned and try again.

Reference: Microsoft Documentation
Prepare for Assured Success
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
New-AzPolicyAssignment doesn't assign the role definition for Managed Identity #10196
saach11 commented Oct 4, 2019 • edited Loading
| When creating a new policy assignment that requires managed identity, it should automatically add the role for the new identity. The policy definition is a custom one with an "effect" = modify. No error after running New-AzPolicyAssignment, the warning can be seen on Policy remediation page |
| The text was updated successfully, but these errors were encountered: |
- 👍 3 reactions
msJinLei commented Oct 8, 2019 • edited Loading
| Could you provide the following information? Please run $PSVersionTable and paste the output in the below code block Please run (Get-Module -ListAvailable) and paste the output in the below code block $DebugPreference='Continue' before running the repro and paste the resulting debug stream in the below code block |
Sorry, something went wrong.
msJinLei commented Oct 11, 2019
| Any update? |

adjohns commented Nov 8, 2019
| I am experiencing the same behavior for the command as saach11 . The identity will be created following the assignment name but then has no role assignments made. When you perform a remediation action it will fail since the assignment powershell did not give the identity any permissions. I have sent you an email with the requested debug information. |
msJinLei commented Dec 19, 2019
| I am experiencing the same behavior for the command as saach11 . The identity will be created following the assignment name but then has no role assignments made. When you perform a remediation action it will fail since the assignment powershell did not give the identity any permissions. I have sent you an email with the requested debug information. Sorry, which address you emailed to? |
DdenBraver commented Jan 15, 2020 • edited Loading
| Is there any update regarding this issue? "New-azPolicyAssignment with -AssignIdentity switch, does not actually assign the identity role" |
adjohns commented Jan 16, 2020 • edited Loading
| - I sent it to your Microsoft email which I found on the GAL - just bumped it today to the top of your inbox. - A workaround we used is to call the 'New-AzPolicyAssignment' CMDLET then follow it with a call to 'New-AzRoleAssignment' using the produced ObjectID and RoleID from the policy assignment creation.
IE: |
- 👍 1 reaction
DdenBraver commented Jan 20, 2020
| Thanks the manual workaround does work indeed. |
ghost commented Jun 20, 2020
| Thanks for the feedback! We are routing this to the appropriate team for follow-up. cc @aperezcloud, . |
dingmeng-xue commented Jun 20, 2020
| Service team, even workaround works as mentioned. Please look into if can be improved. |
kenieva commented Jun 20, 2020
| This is by design. When creating an assignment through portal, the role assignments are auto-granted. However, when using PowerShell, you must manually configure the managed identity. Information found here: |
KamilWiecek commented Oct 8, 2020
| You can use the script you find here: |
No branches or pull requests
Bring Your Own User Assigned Managed Identity
The Bring Your Own User Assigned Managed Identity (BYO UAMI) feature, available with release 2024-06-05 , allows both Greenfield and Brownfield customers to create a new User Assigned Managed Identity (UAMI) during or after the deployment of AMBA-ALZ. It also allows Brownfield customers, who deployed the ALZ pattern when this feature wasn’t available, to use any existing one by configuring a couple of parameters. Thanks to this new feature, it’s now possible to query Azure Resource Graph (ARG) using the Kusto Query Language. Log-based search alerts can now be enhanced to include ARG queries looking at resource tags.
How this feature works
The BYO UAMI feature works by creating a new UAMI in the management subscription and assigns the Monitoring reader role on the parent pseudo root Management Group. With this new feature, it’s now possible to query Azure Resource Graph (ARG) using the Kusto Query Language and to enhance Log-based search alerts that can now query ARG to look at resource tags or properties. It’s enough to enter the necessary parameter values before running the ALZ pattern deployment.
Should Brownfield customers decide to use their own UAMI after the initial deployment, it will be sufficient to enter the parameter values for bringYourOwnUserAssignedManagedIdentity and bringYourOwnUserAssignedManagedIdentityResourceId , leaving the userAssignedManagedIdentityName parameter at its default and the parameter managementSubscriptionId with no values:
Once parameters are set according to your needs, redeploy the AMBA-ALZ pattern and wait for the remediation to happen. You can also start the Policy remediation manually as documented at Remediate Policies .
Conditional deployment behavior
The deployment template has conditions that controls what is being deployed according to the following two scenarios:
A. Customers want to use existing UAMI. In this scenario the deployment will:
Before executing the deployment, ensure that the existing UAMI is assigned the Monitoring Reader role at the pseudo root Management Group. It is probable that the UAMI you provide is located within the Management subscription beneath the Platform management group, whereas the Policy Assignment resides at the LandingZones management group. In this case, for the deployIfNotExists policies to have permission to assign the UAMI to the scheduled query rule, the Managed Identity Operator role must be granted to the system Managed Identity of the Initiative Assignment ( Deploy-AMBA-VM for the Virtual machine initiative, Deploy-AMBA-HybridVM for the Arc-enabled Servers initiative) at the UAMI scope.
- Not deploy any UAMI
- Not assign the Monitoring Reader role
- Set the provided existing UAMI as the identity to be used in the necessary alerts
Here’s a sample extract of the parameter file with the relevant parameter configuration for this scenario:
B. Customers does not have an existing UAMI and want AMBA-ALZ to create a new one. In this scenario the deployment will:
When a new UAMI is created by the deployment template, the Monitoring Reader role is is automatically assigned at the pseudo root Management Group level during the deployment .
- Deploy any UAMI
- Assign the Monitoring Reader role
Where is it used
This new feature is used in Log-search based alerts. At the moment of this release, there’s one alert using it. The alert is part of the new Deploy Azure Monitor Vaseline Alerts for Hybrid VMs policySet added to monitor hybrid virtual machine.
We’re planning to use this feature more in the future and to include it as part of other alerts.
Switching between BYO UAMI and new UAMI
The conditional deployment behavior discussed earlier, allows brownfield customers to switch from a new created UAMI to an existing one and viceversa. Should customers decide to switch, it will be enough to:
- Change the values in the parameter file to match one of the two scenarios previously discussed
- Redeploy the AMBA-ALZ pattern
- Run the remediation for the Deploy Azure Monitor Baseline Alerts for Hybrid VMs policy initiative as documented at Remediate Policies
The code will reconfigure the necessary alerts to use either the customer’s provided UAMI or the new one created during the deployment.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Quickstart: Create a policy assignment to identify non-compliant resources using Azure portal
- 3 contributors
The first step in understanding compliance in Azure is to identify the status of your resources. In this quickstart, you create a policy assignment to identify non-compliant resources using Azure portal. The policy is assigned to a resource group and audits virtual machines that don't use managed disks. After you create the policy assignment, you identify non-compliant virtual machines.
When assigning a built-in policy or initiative definition, it's optional to reference a version. Policy assignments of built-in definitions default to the latest version and automatically inherit minor version changes unless otherwise specified.
Prerequisites
- If you don't have an Azure account, create a free account before you begin.
- A resource group with at least one virtual machine that doesn't use managed disks.
Create a policy assignment
In this quickstart, you create a policy assignment with a built-in policy definition, Audit VMs that do not use managed disks .
Sign in to the Azure portal .
Search for policy and select it from the list.

Select Assignments on the Policy pane.

Select Assign Policy from the Policy Assignments pane.
On the Assign Policy pane Basics tab configure the following options:
| Field | Action |
|---|---|
| Use the ellipsis ( ) and then select a subscription and a resource group. Then choose to apply the scope. | |
| Optional and isn't used in this example. | |
| Skip resource selectors for this example. Resource selectors let you refine the resources affected by the policy assignment. | |
| Select the ellipsis ( ) to open the list of available definitions. | |
| Search the policy definitions list for definition, select the policy, and select . There's a column that shows the latest version of the definition. | |
| Accept the version in format to ingest major, minor, and patch versions. Select the ellipsis ( ) to view available versions and the options to enroll in minor version updates or preview versions. You must select a version to change the options. For more information, go to . | |
| By default uses the name of the selected policy. You can change it but for this example, use the default name. | |
| Optional to provide details about this policy assignment. | |
| Defaults to . For more information, go to . |

After a Policy definition is selected, you can change the Version (preview) options.
For example, if you select the options shown in the image, the Version (preview) is changed to 1.0.* .

Select Next to view each tab for Parameters and Remediation . No changes are needed for this example.
| Tab name | Options |
|---|---|
| If the policy definition you selected on the tab has parameters, you configure them on the tab. This example doesn't use parameters. | |
| You can create a managed identity. For this example, is unchecked. This box be checked when a policy or initiative includes a policy with either the or effect. For more information, go to and . |
Select Next and on the Non-compliance messages tab create a Non-compliance message like Virtual machines should use managed disks .
This custom message is displayed when a resource is denied or for non-compliant resources during regular evaluation.
Select Next and on the Review + create tab, review the policy assignment details.
Select Create to create the policy assignment.
Identify non-compliant resources
On the Policy pane, select Compliance and locate the Audit VMs that do not use managed disks policy assignment. The compliance state for a new policy assignment takes a few minutes to become active and provide results about the policy's state.

The policy assignment shows resources that aren't compliant with a Compliance state of Non-compliant . To get more details, select the policy assignment name to view the Resource Compliance .
When a condition is evaluated against your existing resources and found true, then those resources are marked as non-compliant with the policy. The following table shows how different policy effects work with the condition evaluation for the resulting compliance state. Although you don't see the evaluation logic in the Azure portal, the compliance state results are shown. The compliance state result is either compliant or non-compliant.
| Resource State | Effect | Policy Evaluation | Compliance State |
|---|---|---|---|
| New or Updated | Audit, Modify, AuditIfNotExist | True | Non-Compliant |
| New or Updated | Audit, Modify, AuditIfNotExist | False | Compliant |
| Exists | Deny, Audit, Append, Modify, DeployIfNotExist, AuditIfNotExist | True | Non-Compliant |
| Exists | Deny, Audit, Append, Modify, DeployIfNotExist, AuditIfNotExist | False | Compliant |
The DeployIfNotExist and AuditIfNotExist effects require the IF statement to be TRUE and the existence condition to be FALSE to be non-compliant. When TRUE , the IF condition triggers evaluation of the existence condition for the related resources.
Clean up resources
You can delete a policy assignment from Compliance or from Assignments .
To remove the policy assignment created in this article, follow these steps:
On the Policy pane, select Compliance and locate the Audit VMs that do not use managed disks policy assignment.
Select the policy assignment's ellipsis and select Delete assignment .

In this quickstart, you assigned a policy definition to identify non-compliant resources in your Azure environment.
To learn more about how to assign policies that validate resource compliance, continue to the tutorial.
Tutorial: Create and manage policies to enforce compliance
Was this page helpful?
Additional resources
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
Add a role assignment between two different resource groups using ARM
'Resource Group 1' has user assigned managed identity and active storage accounts. 'Resource Group 2' has passive storage accounts. Now, current ARM template has the definitions for the user managed identity and active storage accounts and within the nested deployment, it has definitions for passive storage accounts which are deployed in 'Resource Group 2'. Now I want to add role assignments between user assigned managed identities and storage acccounts. Role assignments between user assignment managed identity and active storage accounts which are in the same resource group are deploying fine. But I am unable to deploy role assignments between user assigned managed identity in resource group 1 and passive storage accounts in resource group 2.
I have tried adding cross resource group role assignments within the nested deployment where passive storage accounts are defined but I am getting template validation error that the passive storage account is not defined in the template.
ARM template
Below is error message I got while deploying
- azure-resource-manager
- 2 Without sharing the ARM Template it is hard to support you. Generally I would recommend you to use bicep as it is easier to use and diagnose. But speaking about your issue, you should be able to create a nested deployment learn.microsoft.com/en-us/azure/templates/microsoft.resources/… which contains the RBAC assignment and takes the resource id of the resource as input. – Julian Hüppauff Commented Aug 8 at 8:33
- @JulianHüppauff, thanks for your response. I have updated the ARM template and error. Can you please take a look. – Upgrade Commented Aug 8 at 10:26
- The arm tag is for the ARM CPU architecture. I'm guessing you wanted azure-resource-manager here instead, so I added it. Please edit if this is not correct. In general, please check the description of a tag before using it. Welcome to the site! – Nate Eldredge Commented Aug 8 at 16:03
The main issue to seems to be with the way we try to deploy using same RG in which the managed identity is used and also the way we nested the managed identity in the variables
Even though the managed identity was from direct RG we can refer it directly as mentioned in the below configuration.
ARM configuration:
Deployment:

Azure ARM Role Assignment different Resource Group - Stack Overflow by 4c74356b41
Assign Azure roles using Azure Resource Manager templates - Azure RBAC | Microsoft Learn
Adding Role Assignments to Two Different Resource Groups using ARM: Active Storage Accounts in ResourceGroup1 vs. Active Storage Accounts in ResourceGroup2
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged azure azure-resource-manager or ask your own question .
- The Overflow Blog
- At scale, anything that could fail definitely will
- Best practices for cost-efficient Kafka clusters
- Featured on Meta
- Announcing a change to the data-dump process
- Bringing clarity to status tag usage on meta sites
- What does a new user need in a homepage experience on Stack Overflow?
- Feedback requested: How do you use tag hover descriptions for curating and do...
- Staging Ground Reviewer Motivation
Hot Network Questions
- Short story about humanoid creatures living on ice, which can swim under the ice and eat the moss/plants that grow on the underside of the ice
- Is it safe to install programs other than with a distro's package manager?
- Light switch that is flush or recessed (next to fridge door)
- How do I safely download and run an older version of software for testing without interfering with the currently installed version?
- How to securely connect to an SSH server that doesn't have a static IP address?
- Can Christian Saudi Nationals visit Mecca?
- Is this schematic ready to be made into a circuit?
- Getting error with passthroughservice while upgrading from sitecore 9 to 10.2
- Using rule-based symbology for overlapping layers in QGIS
- Does a representation of the universal cover of a Lie group induce a projective representation of the group itself?
- In Lord Rosse's 1845 drawing of M51, was the galaxy depicted in white or black?
- Can I arxive a paper that I had already published in a journal(EPL, in my case), so that eveyone can access it?
- Can a quadrilateral polygon have 3 obtuse angles?
- How to run only selected lines of a shell script?
- Sylvester primes
- How to resolve this calculation prompt that appears after running the drawing program?A Bug in version 14.1.0
- Was the term " these little ones" used as a code word for believers?
- Why does this theta function value yield such a good Riemann sum approximation?
- Will a Cavalier's mount grow upon maturity if it already grew from the dedication?
- What's "the archetypal book" called?
- Can I Use A Server In International Waters To Provide Illegal Content Without Getting Arrested?
- Why do the opposite of skillful virtues result in remorse?
- meaning of "as... as could be"
- Why do sentences with いわんや often end with をや?

IMAGES
VIDEO
COMMENTS
A role assignment policy is a collection of one or more end-user roles that enable users to manage their mailbox settings and distribution groups in Exchange Online. End-users roles are part of the role based access control (RBAC) permissions model in Exchange Online. You can assign different role assignment policies to different users to allow or prevent specific self-management features in ...
Role assignments enable you to grant a principal (such as a user, a group, a managed identity, or a service principal) access to a specific Azure resource. This article describes the details of role assignments.
Learn how to grant access to Azure resources for users, groups, service principals, or managed identities using the Azure portal and Azure role-based access control (Azure RBAC).
We're excited to share the public preview of delegating Azure role assignment management using conditions. This preview gives you the ability to enable others to assign Azure roles but add restrictions on the roles they can assign and who they can assign roles to.
The way you control access to resources using RBAC is to create role assignments. This is a key concept to understand - it's how permissions are enforced. A role assignment consists of three elements: security principal, role definition, and scope. User - An individual who has a profile in Azure Active Directory.
ARM templates can help define Azure Role-Based Access Control. By creating role assignments, users can grant Managed Identities access to resources.
0 We were trying to implement a policy in azure to restrict role based assignment. We referenced below github policy, but during testing we observed it's not evaluating the roledefinitionIds defined in the parameter.
Role Assignment required by Policy - Policy definition (s) specify the required Role Definition Ids. additional Role Assignment - from filed "additionalRoleAssignments" in the Policy Assignment file.
Learn more about Role Assignment Hygiene and how to keep your Azure environment clean.
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
Azure role-based access control (Azure RBAC) has several Azure built-in roles that you can assign to users, groups, service principals, and managed identities. Role assignments are the way you control access to Azure resources. If the built-in roles don't meet the specific needs of your organization, you can create your own Azure custom roles.
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
Azure Policy is a service in Azure, that you use to create, assign and, manage policy definitions in your Azure environment.
Description When creating a new policy assignment that requires managed identity, it should automatically add the role for the new identity. The service principal is created, however the role assignment is not. As a result Policy remediation doesn't work as expected.
For now, There's no feature in azure to restrict global administrator to apply roles only at Security group level and not at user level. Also, there's no Azure policy to restrict this yet. As a workaround, You can have 1 User with global administrator role assigned who can create all the roles for your users and groups.
Describes the policy assignment definition used by Azure Policy to relate policy definitions and parameters to resources for evaluation.
Before executing the deployment, ensure that the existing UAMI is assigned the Monitoring Reader role at the pseudo root Management Group.. It is probable that the UAMI you provide is located within the Management subscription beneath the Platform management group, whereas the Policy Assignment resides at the LandingZones management group.
0 As a part of Azure Governance, I want to deny all the members (owners) from assigning an existing custom role to any user at subscription or resource group level. I'm wondering it is even possible. If so, what would be the policy?
The first step in understanding compliance in Azure is to identify the status of your resources. In this quickstart, you create a policy assignment to identify non-compliant resources using Azure portal. The policy is assigned to a resource group and audits virtual machines that don't use managed disks. After you create the policy assignment, you identify non-compliant virtual machines.
I have a requirement where I need to deny only owners of the resource group to do new role assignments or changes to existing role assignments. Resource group contributors and readers anyways canno...
Enhancing Data Security and Digital Trust in the Cloud by Implementing Client-Side Encryption (CSE) using Azure Apps, Azure Storage and Azure Key Vault. Think.. Think of Client-Side Encryption (CSE) as a strategy that has proven to be most effective in augmenting data security and modern precursor to traditional approaches.
Role assignments between user assignment managed identity and active storage accounts which are in the same resource group are deploying fine. But I am unable to deploy role assignments between user assigned managed identity in resource group 1 and passive storage accounts in resource group 2.